(1) Necessity of information security policies
Generally, in the conventional way of using information systems for the transaction of most administrative activities, only qualified officers or operators were allowed to access the host computer centrally placed for information processing. Information exchange with external circles as well as reports or announcements were generally made verbally or through documents printed on paper. Today, personal computer users are on a sharp increase in offices. This has created an environment where individual workers are allowed to have their information processed, or even access global networks from their own terminal, to help improve the efficiency of administrative activities and services, to a large extent. The number of personal computer users has explosively increased in society generally. The administrative information system is now within easy reach of PC users, both from inside and outside organizational networks. Implementation of the electronic government will make access to the system much easier.
Basically, simplex security measures, which control access to the information system, and to the data inside, would work as long as the source of access is limited to qualified persons. But now, the environment around the information system has changed greatly through the extensive use of general-purpose operating systems and distributed processing, together with development of the IT, and efforts made toward implementation of the electronic government. In addition, access to the system from general people has been made much easier. Expansion of the sources of access to the system also reveals the vulnerability of information systems to unauthorized access. Consequently, the conventional security management system now cannot afford to provide sufficient security, with its physical or technical security measures alone, to protect today's sophisticated networking information systems. The expansion of networking and growth in the number of portable remote terminals, that could encourage unauthorized access, could be negative factors for the systems that make them unstable. We should understand, however, these negative factors can be turned to positive ones, or benefits, if information security is afforded, by managing them appropriately. Sufficient information security has to be provided in the government for stream-lined information exchange with private organizations or foreign countries, based on mutual confidence.
Organizations should set up an integrated information security policy, and have it documented to enhance the sense of security among their staff members, thus preventing any information from being used at the personal discretion of those who handle it.
(2) Characteristics of information security
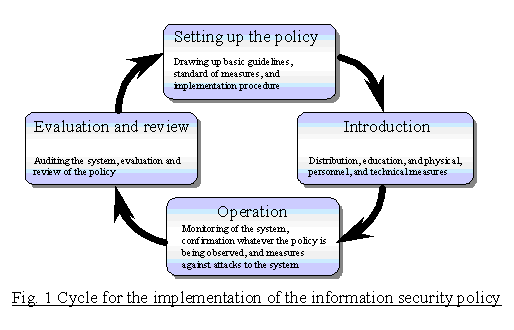
IT evolves so rapidly that the best information security measure employed at one time may not remain the best for long. Continuity is not guaranteed for any hardware or software product that represents the best information security measure at the time of installation. We should understand that information security measures are not complete by simply drawing an information security policy based on these guidelines, but they need constant attention after they are drawn.
The information security policy should also provide a system for constant information collection and security. The policy should be highly comprehensive including appropriate directions, not only about "how an information system should be protected", but also about "what actions should be taken when attacked."
Also required is that the information security policy and the regulations of their implementation, are reviewed periodically. This is an important procedure to check for the presence of any new menaces to the information assets owned by the government ministries and agencies, and for changes to their environment, so that continued measures can be taken. In consideration of rapid advances of information security technologies and hackers' skills that are increasingly becoming more sophisticated, more frequent reviews are important.

As the social economy is going more electronic, spurred by the rapid expansion of the number of Internet users, and the trend toward electronic commerce, the demand for reducing people's work load as to making applications, notifications, and other procedures, is on an explicit increase. Expectations are high for more active communication between the administration and people. The administration environment about information is about to change rapidly. "Basic Guidelines on the Promotion of an Advanced Information and Telecommunications Society" (decided by the Advanced Information and Telecommunications Society Promotion Headquarters on November 9, 1998) aim at the implementation of a highly sophisticated information administration, or the electronic government, at the turn of the 21st century, to follow up the environment change. This means a transfer from information management using the medium paper, to security controlled electronic information management, by the positive use of information communication networks.
The government's information system connected to networks, however, is constantly exposed to the danger of being a victim of wire-tapping, unauthorized access, destruction, tampering, and other malicious actions. The government should keep providing correct information and stabilized administrative services to the people, and maintain security of the information designated as non-disclosure information, including an individual's private information under the Information Disclosure Law (Law Concerning Access to Information held by Administrative Organizations).
Based on the understanding of the matters described thus far, the security levels throughout the government should be raised in accordance with the following basic considerations:
(1) Individual ministries and agencies3 of the government should draw-up an information security policy based on these guidelines for promoting integrated and systematic measures for security. The ministries and agencies should take the necessary actions required, in sequence, with the goal of attaining a security level appropriate for the basis of the electronic government.
The implementation of information security, aimed at by these guidelines, assumes that information, in the form of documents and other media, is appropriately managed. The ministries and agencies should provide necessary measures in this respect to attain an extremely high level of security.
(2) The ministries and agencies should stand firm on these guidelines, and make every effort to raise the information security levels at their local bureaus (Regional bureaus and departments) or semi governmental organizations.
(3) The Cabinet Secretariat (Cabinet Office) should establish a cooperative system, or enhance the system, when it exists, within the government for the solution of various problems common to the ministries and agencies. The problems may include urgent actions in response to unauthorized access, or the proliferation of computer viruses, as well as the education of talented personnel or research and development, for raising the level of security throughout the government.
(4) The ministries and agencies should have access administrators implement appropriate preventive measures against unauthorized access in compliance with the Unauthorized Computer Access Law. This is to prevent government information systems from being utilized for attacks on other information systems.
(5) Cooperation should be tightened between the state and the private sector, through enhanced information exchanges, in order to upgrade the security level of Japan's information communication infrastructure.
(6) The ministries and agencies should evaluate the current information security policy periodically and update it if necessary. They should study about the necessity of change at least one year after the policy was formulated.
The Cabinet Secretariat (Cabinet Office), understanding the whole picture of the implementation status of the information security policy at each ministry and agency, technologies expected in the future, conceivable threats, and other factors, should repeat evaluation and review continually.
3. The Cabinet Secretariat, Cabinet Legislation Bureau, Prime Minister's Office, and Fair Trade Commission are included.
This section provides definitions of the terms that appear in these guidelines.
4) As defined in the standard specified by ISO (ISO 7498-2:1989)
Confidentiality: the quality of a system that ensures only the qualified persons are permitted to access the information inside Integrity: the quality of data protected from alteration, faulty processing, and destruction or loss Availability: the degree to which a system is ready to provide necessary information to a qualified person (For reference)
In addition to confidentiality, integrity, and availability, ISO/IEC JTC 1/SC 27 provides definition of the following three terms that do not appear in this guideline.
Authenticity: the guarantee that the identity of a user, process, system and information, or resources, are true to their respective assertion. Accountability: the guarantee that an action done by a subject permits a path that leads only to that subject to be traced Reliability: the ability to provide a result that matches an intended action
All pieces of information have to be classified according to their level of importance, so that appropriate measures can be provided for each level. Information related to the information system requires special attention different to that of the management of conventional information where paper is the major medium. The Policy has to be provided so that the document management, required of each ministry and agency, will also be implemented in the information system. It should be noted, however, that more appropriate management is required against attacks on information assets of the ministries and agencies from hackers.
The information system consists of hardware, software, data in the recording medium as well as other information, including documents like system configuration diagrams and the like. Out of these components, the target of the policy provided by the ministries and agencies, is the information electromagnetically recorded in the information system, and the operator who handles that information. Therefore, the information that comprises the information assets refers to the electromagnetically recorded information hereafter.
Generally, one integrated policy is drawn-up, which is implemented with procedures provided by individual departments. If the form of the business of a particular department requires that the policy be divided, it can be separated as needed.
Now, the number of documents that can be printed from the electromagnetic medium has drastically increased, making it easy to get multitudes of copies of the same document. Within such an environment, if any problems are found as to the conventional document management during the stage of policy making, appropriate consideration should be given to the management method.
(Example)
|
Target
|
Examples
|
| Information system | Computer machine, basic software, application software, network, communication equipment, recording medium, system configuration diagrams, etc. |
| Information recorded in the system | Access log, electromagnetically recorded documents including diagrams |
| Personnel who handle the information | Personnel including regular workers and part time workers, temporary workers, consignees, etc. |
Disclosure or non-disclosure of information will be determined based on the Information Disclosure Law after it is enforced, although, the final decision is up to the judgement of the relevant ministry or agency. Generally, security problems may arise if all information is disclosed. The scope of disclosure should be determined with careful consideration.
It is important to make public that certain measures are being taken by individual ministries and agencies, as a means to indicate that the ministries and agencies are to deal with the problem. Thus it is desirable that information be made as public as possible.
(1) Obtaining a clear picture of the basic guidelines under which the information security is maintained.
The information assets to be protected from the dangers they are exposed to (wire tapping, unauthorized access, and destruction, tampering, extraction and leakage of data, DoS attack, and other malicious actions) should be specified. Individual information assets should be classified according to their risk levels with consideration given to confidentiality and the environment of their use. The resulting classes of information associated with a specific degree of risk will provide a basis for working out necessary information security measures.
A system for providing information security measures should be established. It should be noted that a number of persons could be involved in the operation of an information system, including a business officer, a system administrator, and users of the system. The responsibility and authority of each person must be made known, so that appropriate information security measures will be provided within the organization.
(2) Attention should be paid to the following for continued maintenance of the policy and its review.